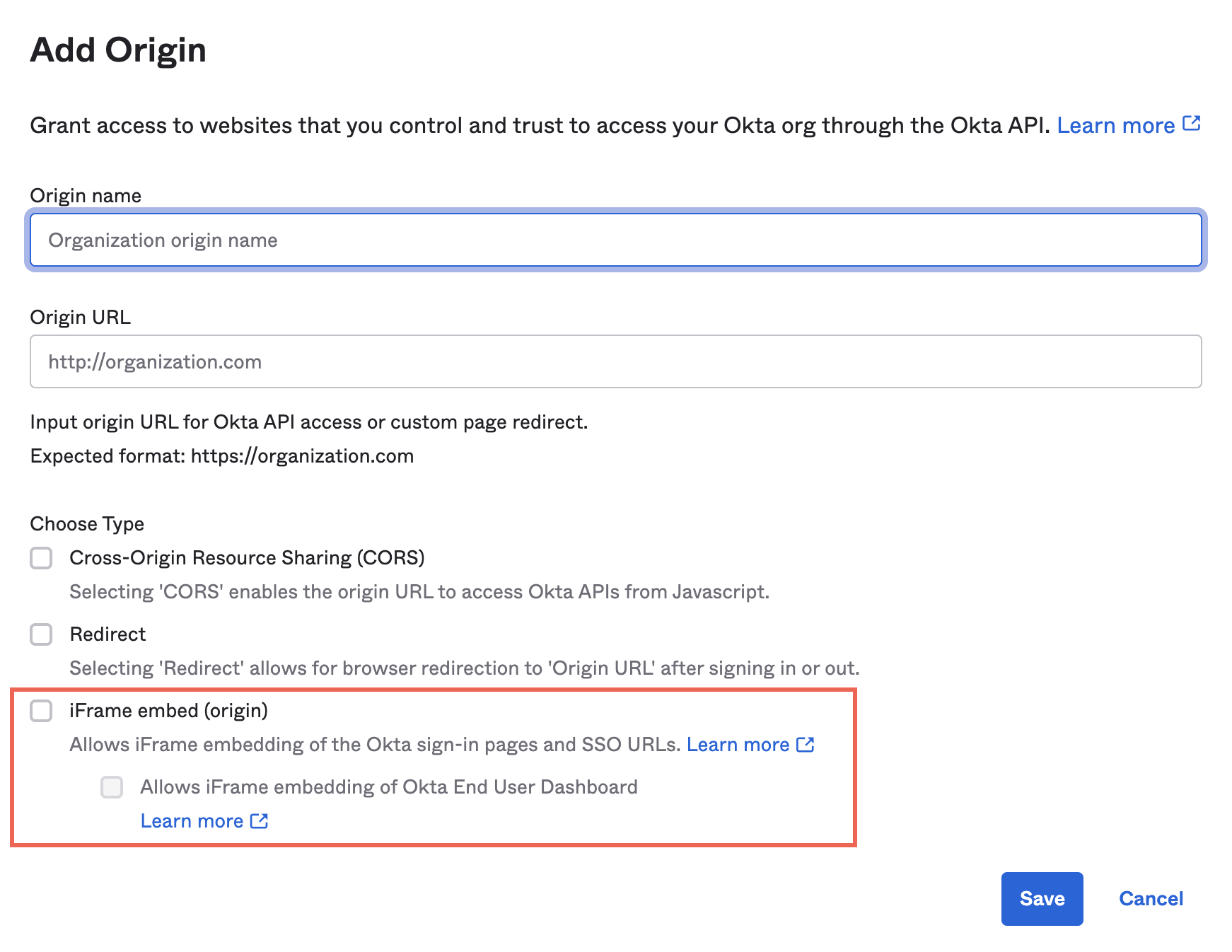
42 identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used.
Solved Match each term to its correct definition. Drag each | Chegg.com Drag each item on the left to its matching item on the right. Note that every item may not have a match, while some items may have more than one match. the study of individual cases that illustrate general economic laws the study of dollars and cents the study of the overall aspects and workings of an economy recorder.butlercountyohio.org › search_records › subdivisionWelcome to Butler County Recorders Office Copy and paste this code into your website. Your Link Name
Identify and label the following attacks by dragging the term on the ... Identify and label the following attacks by dragging the term on the left to the from CMIT- 320 at University of Maryland, University College Study Resources Main Menu
Identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used.
Identify and label the following attacks by dragging the term on the ... Identify and label the following attacks by dragging the term on the left to the from CIS MISC at North Central State College. Study Resources. Main Menu; ... Identify and label the following attacks by dragging the term on the left to the. Identify and label the following attacks by dragging. School North Central State College; Test Out 3 - Subjecto.com You identify the following values: • Asset value = 400 ... Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. Vishing Piggybacking Spam Phishing Whaling en.wikipedia.org › wiki › Social_DarwinismSocial Darwinism - Wikipedia In fact, Spencer was not described as a social Darwinist until the 1930s, long after his death. The term "social Darwinism" first appeared in Europe in 1880, and journalist Emilie Gautier had coined the term with reference to a health conference in Berlin 1877. Around 1900 it was used by sociologists, some being opposed to the concept.
Identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used.. 3.5 Flashcards | Quizlet Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. 1) An attacker convinces personnel to grant access to sensitive information or protected systems by pretending to be someone who is authorized and/or requires that access. Masquerading rationalwiki.org › wiki › Blaire_WhiteBlaire White - RationalWiki Jun 30, 2022 · Blaire White (September 14, 1993–) is a YouTube talker who at one time described herself as a "transgender conservative commentator".[2] Her YouTube channel description previously stated that she "create[s] videos making fun of ideologues and cultural Marxism",[3] but now simply says that she is "your problematic fav".[4] In practice, White's videos either attack "SJW ... EOF coursehelponline.comCourse Help Online - Have your academic paper written by a ... We will take care of all your assignment needs. We are a leading online assignment help service provider. We provide assignment help in over 80 subjects. You can request for any type of assignment help from our highly qualified professional writers. All your academic needs will be taken care of as early as you need them. Place an Order
CyberSecurity Chapter 3 Flashcards | Quizlet Which of the following characteristics are most important when designing an SLA? (select two) 1)clear and detailed descriptions of penalties if the level of service is not provided 2)detailed provider responsibilities for all continuity and disaster recovery mechanisms You plan to implement a new security device on your network. Match each description to its corresponding term. (Not all options are ... message encoding : the process of converting information from one format into another acceptable for transmission message sizing : the process of breaking up a long message into individual pieces before being sent over the network message encapsulation : the process of placing one message format inside another message format afn.netAmerican Family News Aug 02, 2022 · Politics-Govt Just in time for U.S. Senate race, border wall gets a makeover. The “big” and “beautiful” U.S.-Mexico border wall that became a key campaign issue for Donald Trump is getting a makeover thanks to the Biden administration, but a critic of the current president says dirty politics is behind the decision. › newsNews: Breaking stories & updates - The Telegraph Latest breaking news, including politics, crime and celebrity. Find stories, updates and expert opinion.
› opinionOpinion - The Telegraph The miserable truth is that our leaders don’t want us to have cheap energy. Politicians, in hoc to eco-extremists, have come to believe that consuming fuel is intrinsically sinful Chapter 12- InQuizitive Flashcards | Chegg.com Here are five ways in which Neandertals and modern Homo sapiens are either similar or different. Indicate whether each observation shows a similarity between Neandertals and modern Homo sapiens or a difference between the two by dragging the term to the appropriate part of the graphic 1. Similar-Different-Similar 2. Different-Similar en.wikipedia.org › wiki › Social_DarwinismSocial Darwinism - Wikipedia In fact, Spencer was not described as a social Darwinist until the 1930s, long after his death. The term "social Darwinism" first appeared in Europe in 1880, and journalist Emilie Gautier had coined the term with reference to a health conference in Berlin 1877. Around 1900 it was used by sociologists, some being opposed to the concept. Test Out 3 - Subjecto.com You identify the following values: • Asset value = 400 ... Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. Vishing Piggybacking Spam Phishing Whaling
Identify and label the following attacks by dragging the term on the ... Identify and label the following attacks by dragging the term on the left to the from CIS MISC at North Central State College. Study Resources. Main Menu; ... Identify and label the following attacks by dragging the term on the left to the. Identify and label the following attacks by dragging. School North Central State College;



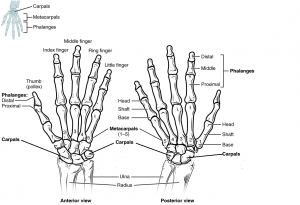














Post a Comment for "42 identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used."